Analysis of the April 2025 BreachForums Outage: Looking at different Claims of DDoS and Law Enforcement Disruption

Executive Summary
With this write up / report I want to look at the likely causes behind the latest disapperance of the Breach Forums aka breachforums.st beginning around April 15, 2025.
BreachForums, a well known English-language marketplace for stolen data and hacking tools, has a well-documented history of disruptions by law enforcement followed by periods of resurgence. The April 2025 disappearance is a little different from previous happenings though, without the usual indicators, such as domain seizure banners or official press releases, that characterized previous law enforcement actions, most recently and notable, the May 2024 seizure. Initial claims attributed the outage to a Distributed Denial-of-Service (DDoS) attack by a group called the Dark Storm Team; however, these claims remain unverified and lack credibility given the other surrounding events.
When we analyze the currently available information, sourced from a mix of cybersecurity reporting and community observations, we can not help but to suspect that an undisclosed law enforcement action is the most probable cause of the recent disruption. Key indicators supporting this assessment include the sudden, unexplained nature of the outage, the reported compromise and redirection of the administrator "Anastasia's" Telegram account to an FBI-controlled channel, and the simultaneous disappearance or unusual activity of key forum moderators "ShinyHunter" and "Hollow".
These events are very similar, even identical, to tactics observed during confirmed law enforcement operations against BreachForums and its predecessors in 2024 and 2023. While we have yet to get any definite confirmation, the theory of a Law Enforcement operation being the cause outweighs the likelihood of a simple technical failure or the uncorroborated DDoS claims.
BreachForums: A Cycle of Disruption and Resurgence
To better understand the current outage we need to look back at the turbulent history of BreachForums and its predecessor, RaidForums. These platforms have consistently served as central hubs within the English-speaking cybercrime ecosystem, facilitating illicit trade and communication, but their operations have been interrupted by law enforcement actions quite a few times, only for them to reappear, demonstrating significant resilience. That by the way is something that many large legal corporations could learn a thing from, or two.
Introduction to BreachForums
BreachForums, sometimes referred to as Breached, has long established itself as a prominent English-language cybercrime and black-hat hacking forum. It was established primarily as an alternative and direct successor to RaidForums, another major illicit forum that was shut down and seized by law enforcement in early 2022. Like RaidForums, BreachForums facilitated the discussion of hacking topics and served as a marketplace for distributing stolen data, including credentials, personally identifying information (PII), financial data, compromised databases, hacking tools, and various other illicit services. Before the first major disruption by Law Enforcement, the forum was able to amass quite a substantial user base, exceeding 340,000 members.
The Pompompurin Era and Initial Takedown (March 2022 - March 2023)
The original version of BreachForums was launched in March 2022 by Conor Brian Fitzpatrick, a then-19-year-old operating under the alias "Pompompurin". The forum quickly gained popularity, filling the void left by the takedown of RaidForums.
This first era came to an end in March 2023 when Fitzpatrick was arrested by U.S. law enforcement in Peekskill, New York. He was subsequently charged with conspiracy to commit access device fraud and later pleaded guilty to additional charges, including possession of child pornography. Fitzpatrick ultimately received a sentence of time served followed by 20 years of supervised release, a sentence the U.S. government has appealed.
Following Fitzpatrick's arrest, another forum administrator known as "Baphomet" initially took control of the site's infrastructure. However, citing concerns that law enforcement had gained access to the forum's servers and potentially user data after the arrest, Baphomet announced the shutdown of this first version of BreachForums (often hosted at domains like breached.vc or .to) on March 21, 2023. The FBI later confirmed they had indeed obtained access to the backend database of this version of the forum. The clear web domains associated with this version were formally seized by U.S. authorities in June 2023.
The Baphomet/ShinyHunters Era and Second Takedown (June 2023 - May 2024)
Despite the shutdown and subsequent domain seizure, the demand for a platform like breached persisted, and grew. Around June 2023, a new version of BreachForums was born, reportedly operated by the administrator "Baphomet" in collaboration with the notorious hacking group "ShinyHunters". This version of the forum commonly used domains such as breachforums.st, .cx, .is, and .vc. Initially, there was significant skepticism within the cybercrime community regarding the legitimacy of this new forum, with widespread speculation that it might be a law enforcement honeypot designed to entrap users. Given the previous tactics of the FBI and other law enforcement agencies, this was not entirely unrealistic, in fact, it was quite likely. However, confirmations, including a PGP-signed message allegedly from Baphomet, helped establish its credibility among users yet once again.
This second major version of the forum was operated until May 15, 2024, when it was subjected to a significant and overt law enforcement takedown. This operation, led by the FBI and U.S. Department of Justice (DOJ) with assistance from international partners (including agencies in Australia, Iceland, New Zealand, Switzerland, the UK, and Ukraine), involved placing seizure banners on the forum's clearnet domains (including breachforums.st) and its Tor onion site. More importantly, law enforcement also seized control of the official BreachForums Telegram channel and other channels operated by Baphomet, posting messages confirming the seizure and soliciting information from users. The seizure notice indicated that authorities were reviewing the site's backend data, potentially exposing member information like email addresses, IP addresses, and private messages. This seizure occurred shortly after data allegedly stolen from a Europol portal (EPE) was leaked on the forum, although the timing may have been coincidental given the planning required for such operations. Following the seizure, ShinyHunters announced via Telegram that Baphomet had been arrested.
In a funny twist of events, control of the breachforums.st domain appeared to be regained by forum operators (reportedly ShinyHunters) just hours or days after the FBI seizure banner appeared. The site briefly redirected users to a Telegram channel before reportedly coming back online around May 29, 2024, hosting a major alleged data leak from Ticketmaster/Live Nation. This rapid reappearance further fueled speculation about the forum potentially operating as a law enforcement honeypot.
The Post-Seizure Landscape (Late 2024 - Early 2025)
Following the dramatic events of May 2024, the leadership structure of the forum reportedly underwent further changes. Some sources indicated that the prominent threat actor known as "IntelBroker" assumed ownership or at least operational leadership in 2024, potentially due to stagnation under the previous administration. Subsequently, in early 2025, IntelBroker purportedly announced stepping down, transferring ownership to a user known as "Anastasia". (It is important to note these specific leadership changes in late 2024/early 2025 are primarily cited in Wikipediabased on other sources, and require careful consideration).
Table: Timeline of Key BreachForums Events and Leadership Changes
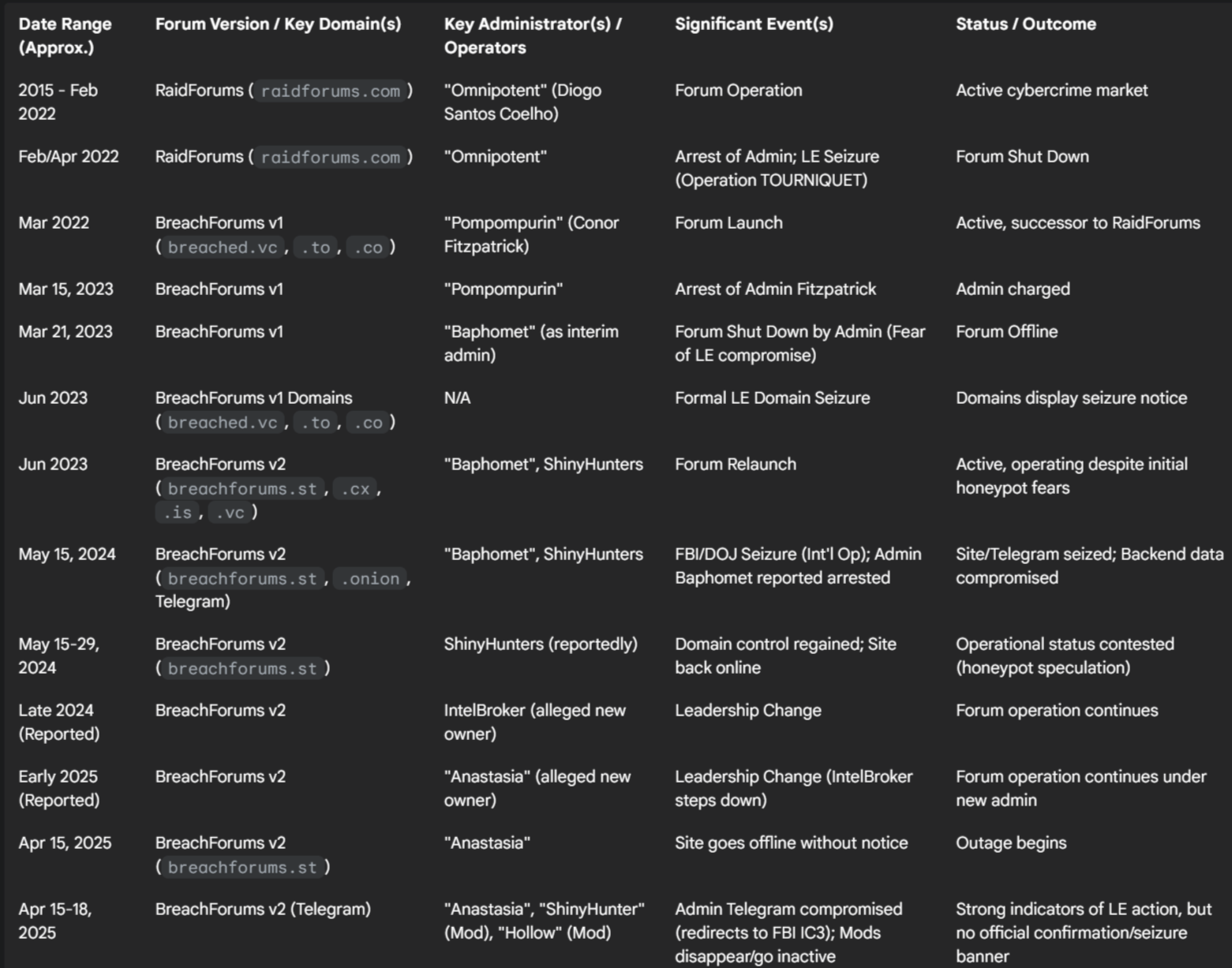
The Pattern of Law Enforcement Takedowns and Forum Resilience
The history detailed above, particularly the sequence involving RaidForums and the first two versions of BreachForums, show us a distinct and recurring pattern. A major forum establishes itself as a central marketplace, operates for a period, attracts significant law enforcement attention leading to disruption (typically involving the arrest of key administrators and seizure of infrastructure), experiences a temporary shutdown, and is then rapidly succeeded by a new version or a rival platform aiming to capture the displaced user base and market demand.
The takedown of RaidForums in 2022 was almost immediately followed by the launch of BreachForums v1 by Pompompurin. Similarly, the arrest of Pompompurin and the shutdown of BFv1 in March 2023 paved the way for the launch of BFv2 under Baphomet and ShinyHunters just months later. Even the overt FBI seizure of BFv2 in May 2024 saw the domain rapidly reappear, albeit under contested circumstances.
This cyclical nature suggests that law enforcement actions, while successful in disrupting specific operations and apprehending key individuals, often function more like temporary setbacks than permanent solutions for the broader cybercrime ecosystem. The underlying demand for stolen data and illicit services remains, and the community demonstrates a capacity for rapid adaptation and reorganization. New leaders emerge, new domains are registered, and users migrate, repeating the cycle. This raises fundamental questions about the long-term effectiveness of solely focusing on takedowns ("whack-a-mole") compared to potentially complementary strategies like sustained infiltration, monitoring for intelligence gathering, or disrupting the financial incentives driving these markets.
Analysis of the April 2025 breachforums.st Outage
This is probably why you are here, so lets start.
The outage of breachforums.st which was observed starting around April 15, 2025, presented a complex situation with multiple potential explanations circulating within the cybersecurity community. A careful examination of the timeline and available evidence is necessary to assess the credibility of these explanations.
Timeline of Observed Events (Mid-April 2025)
The key events surrounding the outage unfolded very rapidly:
- On or around April 15, 2025: The
breachforums.stwebsite becomes inaccessible without any prior warning or announcement from the site administrators. Notably, unlike the May 2024 event, no law enforcement seizure banner was displayed on the domain at this time. - On or around April 15, 2025: The Telegram handle associated with the forum's administrator, "Anastasia," is reportedly compromised. Observers noted that the handle was taken over and began redirecting users to an official FBI Internet Crime Complaint Center (IC3) channel.
- On or around April 15, 2025: Concurrent with Anastasia's Telegram compromise, unusual activity is reported regarding key forum staff. A moderator known as "ShinyHunter" (distinct from the ShinyHunters group previously involved in administration) allegedly removed other staff members from an internal Telegram group before deleting their own Telegram account. Another moderator, "Hollow," reportedly stopped all communication and altered their Telegram visibility settings.
- April 15, 2025: Rumors begin circulating about the potential arrest of "IntelBroker," a high-profile threat actor closely associated with BreachForums. These rumors originated from a post on a newly created Telegram channel but lacked any verifiable evidence.
- Early April 16, 2025 (ET): Claims emerge on Telegram attributing the site's downtime to a DDoS attack perpetrated by a group calling itself the "Dark Storm Team".
- On or around April 18, 2025: Based on the preceding events (admin Telegram compromise, moderator disappearances, activity on an alleged FBI-linked Telegram channel), speculation intensifies within the cybersecurity community, with sources like ransomware affiliate "Rey" on X suggesting a potential FBI seizure or disruption operation.
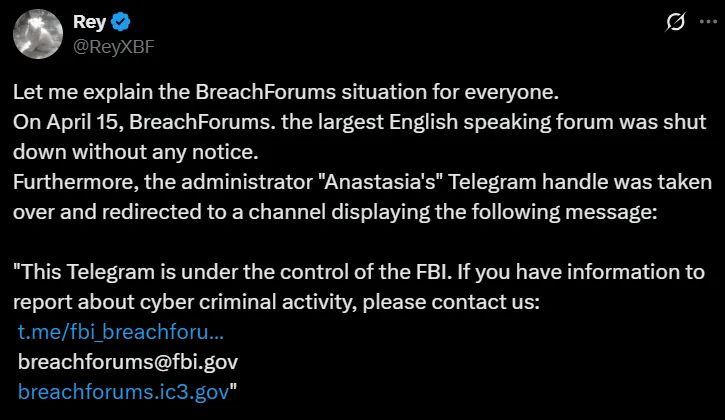
Assessment of the DDoS Claim
The claim that the Dark Storm Team executed a DDoS attack causing the outage surfaced shortly after the site went down. However, this explanation seems not very likely, and here is a few reasons why:
- Lack of Corroboration: No independent sources or consensus among cybersecurity experts emerged to validate Dark Storm's involvement. Such claims from relatively unknown or self-proclaimed hacktivist groups require some level of healthy skepticism.
- Potential Ulterior Motives: Experts noted that claims from groups like Dark Storm might serve purposes other than factual reporting, such as generating confusion, gaining notoriety, or even promoting their own services. It was reported that Dark Storm markets DDoS tools, making the claim potentially a form of advertising. What could be a better selling point than "our tool is the one who bruoght down breached forums".
- Inconsistency with Other Events: A DDoS attack alone would not explain the simultaneous, specific, and targeted actions observed against the forum's administrator and moderators via their Telegram accounts.
Given the lack of verification, potential conflicts of interest, and the inability of this claim to account for the full scope of observed events, the DDoS attack is considered an unlikely primary cause for the sustained outage beginning April 15, 2025.
Assessment of Potential Law Enforcement Action
The possibility of this being the result of some major law enforcement intervention gained significant traction due to several compelling, albeit circumstantial, pieces of evidence:
- Sudden Unexplained Outage: The abrupt cessation of service without admin notice is consistent with a number of previous LE takedowns.
- Compromise of Admin Communications: The reported takeover of Admin Anastasia's Telegram handle and its redirection to an FBI IC3 channel is a particularly strong indicator. Maybe the strongest one. This action directly mirrors the confirmed LE tactic used against administrator Baphomet during the May 2024 seizure, where LE gained control of his Telegram account and used it to communicate.
- Simultaneous Disruption of Leadership: The concurrent disappearance or unusual activity of key moderators (ShinyHunter, Hollow) alongside the admin compromise points towards a coordinated action targeting the forum's operational structure.Disrupting leadership is a absolute trademark of LE operations aimed at dismantling such platforms.
- Alleged FBI Telegram Activity: Reports of activity on a Telegram channel purportedly linked to the FBI and BreachForums further fueled speculation about an ongoing LE operation.
However, a critical counterpoint does exist and can not be left out of the quotation here: the complete absence of official confirmation or the overt tactics used previously. As of the dates covered by the research materials (up to late April 2025 and subsequent checks on historical LE announcements), no FBI or DOJ press releases specifically mentioned a takedown or action against BreachForums in April 2025. Furthermore, the breachforums.st domain itself did not display the characteristic seizure banner that was prominently used in the May 2024 operation. It also did not have the same telltale DNS changes observed, at least until the time of this writing today:
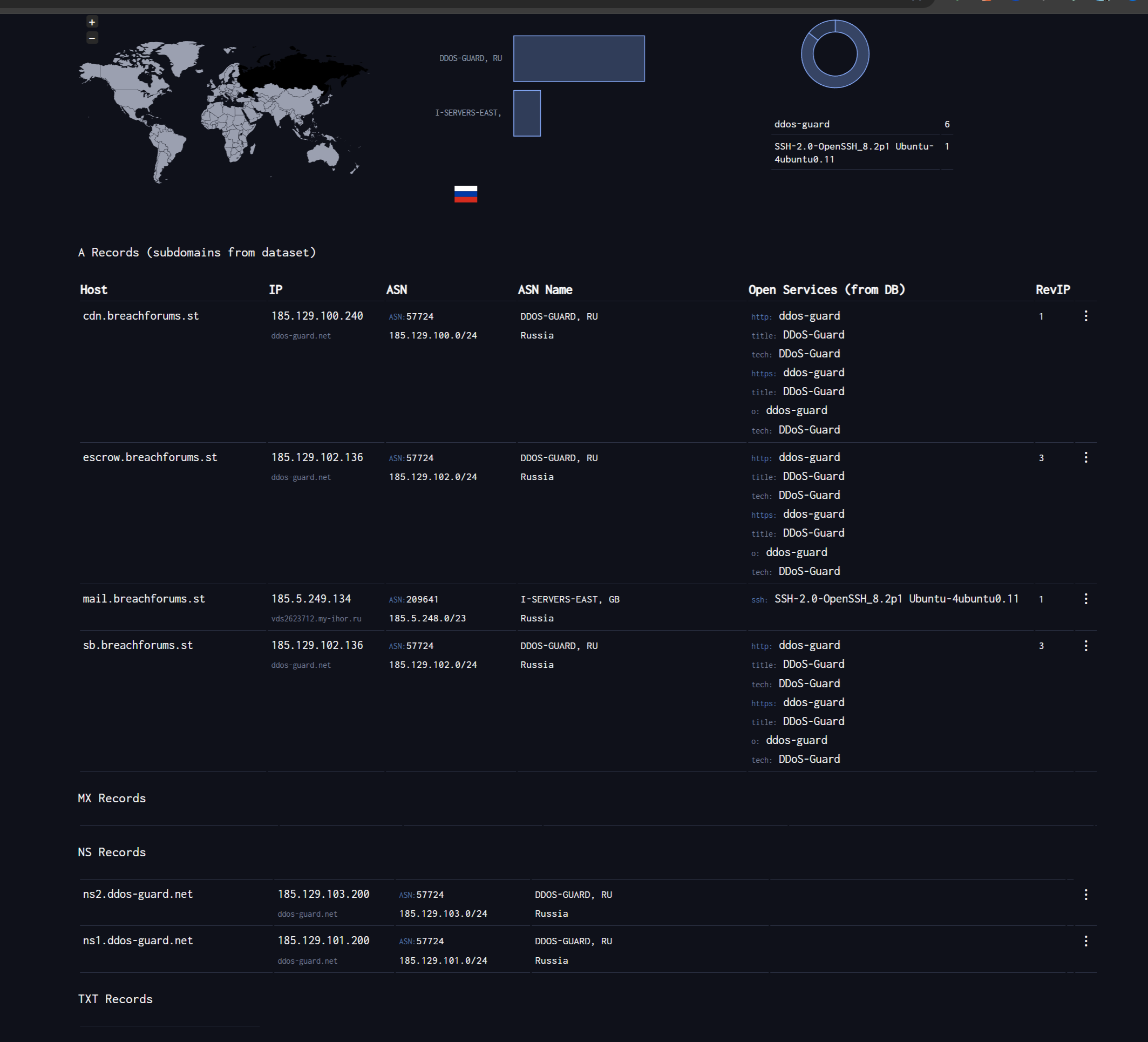
This discrepancy between the strong internal indicators witnessed by the community and the lack of external, official confirmation or overt seizure methods is significant. The May 2024 seizure was public and well-documented, involving clear banners, Telegram messages from LE via seized accounts, likely arrests, and subsequent media reporting citing LE actions. The April 2025 event shared the internal disruption patterns (admin/mod compromise) but entirely lacked the public-facing elements. This divergence could imply several scenarios: perhaps a covert law enforcement operation was underway, prioritizing intelligence gathering or avoiding tipping off remaining targets, thus delaying public announcements or seizures. Alternatively, it could point to a sophisticated internal collapse or power struggle that coincidentally mimicked LE disruption patterns. A third possibility is a targeted LE action focused solely on neutralizing key personnel and communication channels without immediately seizing the primary domain infrastructure. Regardless, the lack of official transparency inevitably fuels speculation and uncertainty within the cybercrime community.
Status of Forum Leadership and Key Figures
The events of mid-April 2025 clearly indicate a significant disruption to the forum's leadership structure:
- Administrator "Anastasia": Reported compromise of their Telegram account, redirecting to an FBI channel, strongly suggests loss of control and potential LE intervention. Their status following this remains unknown based on the available information.
- Moderators "ShinyHunter" and "Hollow": Their simultaneous disappearance – one deleting their account after removing staff, the other becoming unresponsive – points to either direct involvement in the disruption (e.g., arrest/compromise) or a reaction to the perceived LE action against the administrator.
- "IntelBroker": Despite rumors circulating on April 15, 2025, via an unverified Telegram post, there is no corroborating evidence within the provided research materials to confirm the arrest of IntelBroker during this timeframe. IntelBroker is a highly significant figure linked to BreachForums and numerous claimed high-profile data breaches targeting government and corporate entities. An arrest would be major news, yet confirmation is lacking for the April 2025 period.
The simultaneous removal or neutralization of the primary administrator and key operational staff represents a critical blow to the forum's functionality. Cybercrime forums depend heavily on their leadership for maintaining infrastructure, enforcing rules, managing disputes, and curating content. Past takedowns of BreachForums and RaidForums consistently involved targeting the administrators. The events affecting Anastasia, ShinyHunter (moderator), and Hollow in April 2025 created a leadership vacuum that would, at minimum, cause significant operational disruption and contribute directly to the observed outage, irrespective of the precise underlying cause (LE or internal).
Assessment of Technical Issues
While simple technical problems like server failures, database corruption, or critical configuration errors can cause website outages, there is no specific information in the analyzed sources pointing to such issues as the cause of the April 2025 BreachForums downtime. One also needs to consider the amazing resiliance that the forum has shnowed in the past, recovering from major takedowns in days, this shows a significant level of technical expertise and infrastructure readiness to counter such simple failures which makes it even less likely. The concurrent suspicious activities involving the administrator's Telegram account and the disappearance of moderators make a simple, non-malicious technical failure appear less probable as the primary explanation for the sustained outage.
Synthesized Conclusion on the Likely Cause (April 2025 Outage)
Evaluating the potential causes for the breachforums.st outage starting April 15, 2025, needs a look at the evidence for each scenario:
- DDoS Attack: A claim was made by the "Dark Storm Team", but it remains unverified, potentially self-promotional, and fails to explain the targeted actions against forum leadership's communication channels. This is assessed as highly unlikely to be the primary cause. Personally, I rule this out.
- Technical Failure: Standard technical problems are always a possibility for any website outage. However, no evidence surfaced to support this, and it does not align with the specific, coordinated-appearing disruptions affecting the forum's administration and moderation team. This is assessed as less likely than LE action. For the reasons mentioned above, I also tend to rule this out.
- Law Enforcement Action: This scenario is supported by strong circumstantial evidence: the sudden outage, the compromise of the administrator's Telegram account mirroring confirmed LE tactics from the May 2024 seizure, and the simultaneous disappearance of key moderators. The primary counter-evidence is the lack of official confirmation (press releases) or overt indicators (seizure banners) typically associated with such operations. Maybe LE just got smarter on how they do things, possible after all.
Most Probable Scenario: Based on the available intelligence, the convergence of multiple specific indicators—particularly the compromise of administrative communication channels using methods consistent with past FBI actions and the simultaneous neutralization of key staff—points towards an undisclosed law enforcement operation as the most probable primary cause of the April 2025 breachforums.st outage. The specific nature and goals of this potential operation remain unclear due to the lack of official disclosure.
Acknowledging Uncertainty: It must be emphasized that this conclusion is an assessment based on analyzing reported events and patterns from reliable cybersecurity sources. Without official confirmation from law enforcement agencies or direct evidence from the forum operators, absolute certainty is not possible. The possibility of an internal forum collapse engineered to mimic law enforcement action, while seemingly less likely, cannot be entirely dismissed.
Implications and Future Outlook
The recent disruption of BreachForums, regardless of the exact cause, carries significant implications for the cybercrime landscape and highlights the ongoing dynamics between illicit online communities and law enforcement efforts. But it also carries some implications on Cybersecurity researchers for whom the forum always was a treasure throve of information, and for the OSINT community.
Impact on the BreachForums Community
The immediate effect of the outage was the disruption of a major hub for trading stolen data and cybercrime tools. Users were cut off from the platform, likely forcing them to seek alternatives. Past disruptions have shown that users tend to migrate to other existing forums (such as Exploit, XSS, or emerging contenders like LeakBase or ExposedVC) or shift communications to more decentralized or encrypted channels, particularly Telegram groups. The circumstances surrounding the recent outage, especially the suspected LE involvement without overt confirmation and the history of the May 2024 seizure/reappearance, likely amplified existing paranoia within the community regarding LE infiltration and the possibility of forums operating as honeypots. This heightened suspicion can fragment the community and make users more cautious about trusting any single platform.
The Whack-a-Mole Phenomenon
The history of RaidForums and BreachForums exemplifies the persistent challenge often described as the "whack-a-mole" problem in combating cybercrime forums. Each successful takedown creates a vacuum that is quickly filled by successors eager to capture the market share and user base. The announcement by threat actor "USDoD" of plans to launch a new forum called "Breach Nation" shortly after the May 2024 seizure of BreachForums v2 is a concrete example of this dynamic. Other forums like LeakBase and ExposedVC were also noted as potential successors or beneficiaries of BreachForums' downtime. This resilience suggests that simply removing platforms and administrators, while disruptive, does not address the root causes or the persistent demand that fuels these illicit marketplaces.
Evolving Law Enforcement Tactics vs. Cybercrime Adaptation
The potential difference in LE tactics between the overt May 2024 seizure (banners, announcements) and the more covert indicators of the April 2025 disruption (admin Telegram takeover, lack of public confirmation) could signal an evolution in strategy. Law enforcement might be opting for less visible disruptions to facilitate longer-term intelligence gathering, identify more users, or conduct parallel investigations before making public moves. Conversely, the cybercrime community constantly adapts. This includes diversifying communication channels (heavy reliance on Telegram), improving operational security (though often imperfectly, as arrests demonstrate), and rapidly migrating to new platforms when existing ones are compromised or shut down.
The role of platforms like Telegram is particularly noteworthy. Its features facilitate communication and community building for cybercriminals, offering a degree of resilience when forums are down. However, Telegram also presents a significant vulnerability. As demonstrated in both the May 2024 and suspected April 2025 incidents, the seizure and control of key administrator or official forum Telegram accounts by law enforcement can be highly disruptive.It not only cuts off a primary communication channel but also provides LE with a direct means to disseminate information (or disinformation), solicit intelligence from users, and potentially identify individuals through associated account data. This reliance on a centralized, albeit encrypted, platform creates a critical point of failure for forum operations.
Parting words
The April 2025 outage of breachforums.st, most likely precipitated by an unconfirmed law enforcement action, serves as another illustration of the inherent instability and risk associated with participating in cybercrime forums. While LE actions demonstrably disrupt operations and lead to arrests, the cybercrime ecosystem shows remarkable adaptability, ensuring that the demand for such platforms is consistently met by new entrants. The cycle of forum creation, operation, takedown, and succession appears likely to continue. Continuous monitoring of the cybercrime landscape, including emerging forums and communication channels like Telegram, alongside analysis of law enforcement actions and announcements, remains essential for understanding current threats and anticipating future developments.
Update April 28, 2025
A PGP signed message appeared that seems to confirm the Law Enforcement Theory:

And as usual, if you like my articles, buy me a coffee ☕

