Tails OS: The Ultimate Privacy-Focused Operating System
Introduction

Introduction
In today’s digital age, privacy and security have become major concerns. With the increasing level of surveillance we are confronted with and the data breaches we read about almost daily, we all seek ways to protect our online activities and maintain a certain level of anonymity. A great solution that helps us with that is Tails OS, an operating system designed with a strong focus on privacy and security. This comprehensive guide will give you all the necessary information to effectively understand and utilize Tails OS. It will also guide you through the steps to start using it.
What is Tails OS?
Tails OS, short for “The Amnesic Incognito Live System,” is a powerful, robust, Linux-based operating system built for privacy-conscious users. As the name suggests, it offers an amnesic incognito live system, allowing users to run it from a USB stick, DVD, or SD card without leaving traces on the host computer. Tails OS routes all internet traffic through the Tor network, providing more or less anonymous communication and encrypting data to protect user privacy.
Features of Tails OS
Tails OS comes with a range of features that make it an ideal choice for privacy-focused individuals:
1. Built-in Tor Functionality
Tails OS comes pre-configured with built-in Tor functionality. This ensures all internet traffic is routed through the Tor network, providing anonymity and preventing tracking.
2. Pre-configured Security and Privacy Settings
Tails OS is designed with security and privacy in mind. It includes pre-configured security and privacy settings to minimize vulnerabilities and protect user data. Remember that there is no absolute privacy, anonymity, or security. You may have to pay a heavy price for that illusion.
3. Persistent Encrypted Storage
Tails OS offers persistent encrypted storage, allowing users to save sessions between restarts. This ensures that any changes made while using Tails OS are securely stored and accessible in subsequent sessions. There are things to be said for and against that. For example, with persistent storage, you can install additional applications, but if not configured right, those applications may compromise your privacy and/or security. It will also let you change certain configurations, but that too can compromise the very reason why you are using Tails OS in the first place.
4. Secure Erasure of Volatile Memory
Tails OS securely erases volatile memory (RAM) upon shutdown, leaving no traces of activity on the host computer.
5. Automatic Data Encryption and Decryption
Tails OS automatically encrypts and decrypts data, providing additional security for user files.
6. No Traces Left on the Computer
Since nothing is installed or written to the host’s disk, Tails OS leaves no traces of activity on the host computer, ensuring maximum privacy and anonymity.
7. Compatibility with Multiple Operating Systems
Since it boots directly from USB, Tails OS is compatible with Windows, macOS, and Linux systems, allowing users to run it on various platforms, excluding, for now, the Apple Silicon Macbooks
8. Free and Open-Source Software
Tails OS is free and open-source, meaning it can be freely used, modified, and distributed by anyone. This promotes transparency and community collaboration to enhance security and privacy.
9. Portability
Tails OS is portable and usually runs from a USB drive, making it convenient for users who require a secure operating system while traveling.
10. Pre-installed Privacy and Security Tools
Tails OS comes with a wide range of pre-installed privacy and security tools. There is the Tor Browser, Pidgin instant messenger with OTR support, VeraCrypt for file encryption, KeePassXC password manager, and Electrum Bitcoin wallet, among others.
Installation and Setup
Installing and setting up Tails OS is a straightforward process. The following steps guide you through the installation process.
You will need the following:
- A USB Stick or SD Card with at least 8GB of Storage; if you plan on using persistence, calculate the needed size accordingly
- Internet connection to download the image and other tools needed
- At least an hour time if you do this for the first time
- Another device to use for online research in case the booting does not work immediately.
1. Downloading the Tails OS Image
First, download the Tails OS image from the official Tails website. Ensure that you download the correct version for your system.
As mentioned, I am doing this on MacOS; the image is 1.3 GB in size

2. Verifying the Image
Verify the authenticity and integrity of the downloaded Tails OS image using the provided signature. This step helps prevent compromised or tampered downloads that may be manipulated and loaded with malware.
To do this, just follow the step on the tails website, you can either use the offered verification tool or download the PGP Signature
The outcome should be similar to this.

3. Creating a Bootable USB Drive
Create a bootable USB drive using tools like Rufus or Etcher. I am using Etcher here; you can get a download link directly on the Tails website
https://tails.net/etcher/balenaEtcher.dmg
Just plug in your target USB stick and open up Etcher, and the rest is straightforward
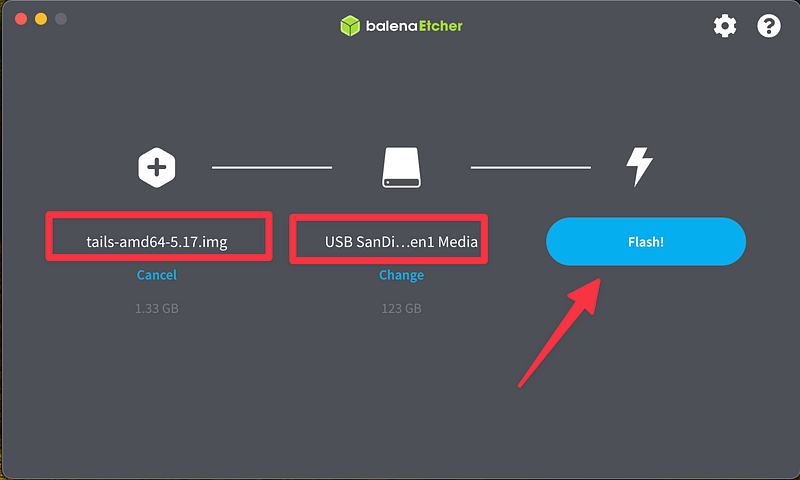
Let the Flash process finish, it shouldn't take too long.
4. Configuring BIOS Settings
This may or may not be needed for you. Access your computer’s BIOS settings and change the boot device priority to boot from the USB drive. This step may vary depending on the manufacturer and BIOS version.
Note: I did this process on a MacBook Pro with M2 Chip. At the time of this writing, Tails does NOT work on MacBooks with Apple Silicon; it does work on older Macs with Intel Chip.
That’s it. You can boot any PC/Laptop into your Tails OS using this USB device you created.
Booting my older Lenovo T480 (an excellent Laptop, by the way, for investigations and other work) with the newly created USB Stick:
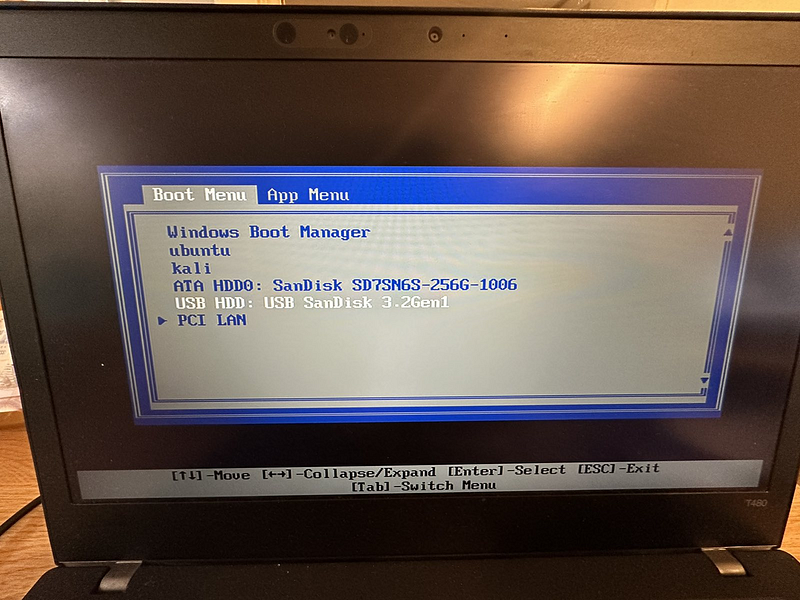
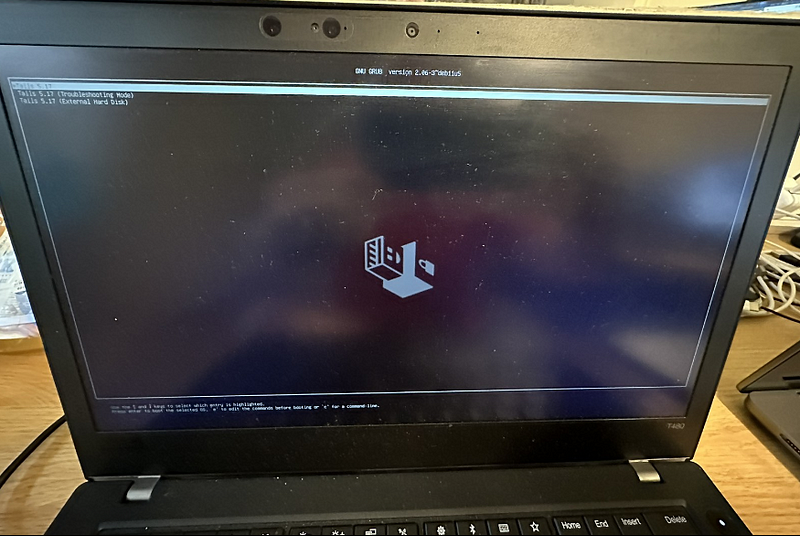
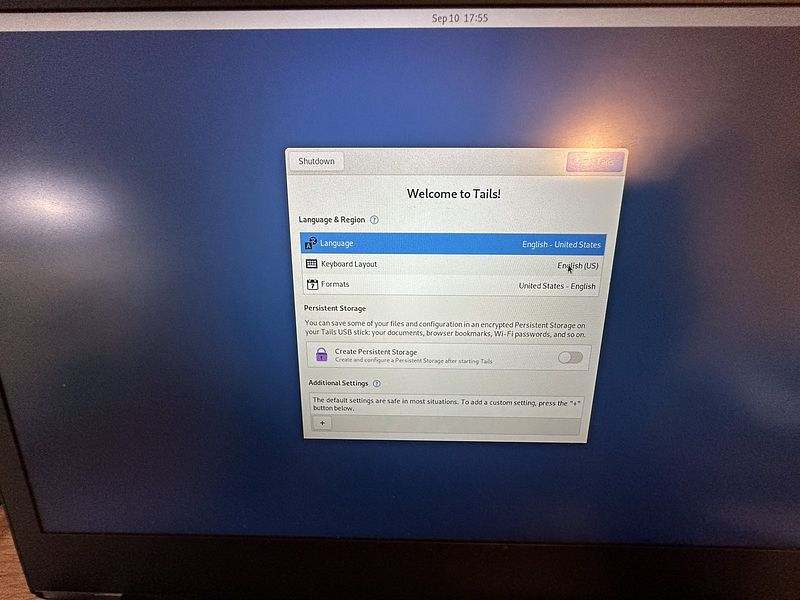
A few more things to say
Benefits of Using Tails OS
Using Tails OS offers several benefits for anybody concerned about their privacy and security:
1. Enhanced Security
Tails OS provides robust security features, including encryption, anonymization through the Tor network, and secure erasure of volatile memory. These features protect user data and prevent unauthorized access. The fact that nothing remains on the host machine you booted your Tails OS instance from makes it a great travel companion.
2. Anonymity and Privacy
Tails OS ensures anonymity and privacy by routing all internet traffic through the Tor network, preventing tracking and keeping users’ online activities private. I want to repeat, though, that there is no 100 percent anonymity, privacy, or security, so act accordingly.
3. Portability and Convenience
With its ability to run from a USB drive, Tails OS offers portability and convenience. Users can carry their secure operating system in their pockets and use it on any compatible computer.
4. Free and Open-Source
Tails OS is free-to-use and open-source software, enabling users to benefit from community-driven development and transparent security practices.
5. Pre-installed Privacy and Security Tools
Tails OS comes with a comprehensive suite of pre-installed privacy and security tools, eliminating users needing to install them separately. This saves time and ensures a secure environment out of the box. You can expand those tools if you choose persistence, but remember what I said about persistence earlier in the article.
Optimizing Tails OS: Tips and Tricks
To optimize your Tails OS experience and further enhance your privacy and security, consider following some of the following tips and tricks:
1. Enable MAC Address Spoofing
MAC address spoofing randomizes your device’s MAC address, making it more difficult for network administrators and online trackers to identify and track it. Mac Address Anonymization is turned on by default, if you need to turn it off for some reason, you can do so by clicking the plus sign on the start screen.

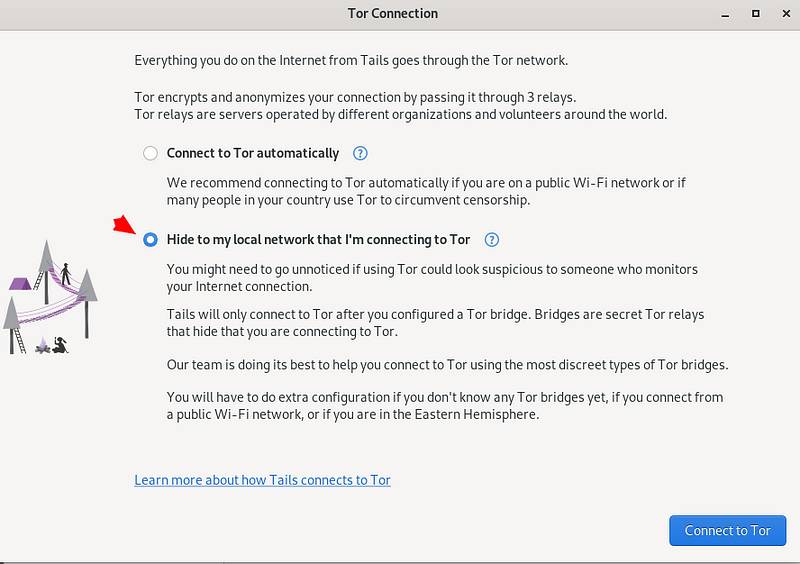
2. Use Bridges to Bypass Censorship
If you are in a region with heavy internet censorship, utilize bridges to access the Tor network. Bridges are private relays that help bypass censorship and provide access to the Tor network. Bridges may also help with ISPs that block TOR traffic even in relatively free countries; it happens.
You can choose that on the following screen, which you will see after the initial startup screen; once you choose to “Start Tails”
3. Create Strong Passwords
Create strong and unique passwords for your Tails OS accounts and encrypted volumes. Strong passwords significantly enhance the security of your data. Obviously, this is a general good practice and not limited to the use of Tails OS.
4. Use the Unsafe Browser Sparingly
The Unsafe Browser in Tails OS is designed for accessing websites that may be blocked or require additional plugins. However, since it runs outside the Tails OS sandbox, use it sparingly and only when necessary to minimize potential security risks.
6. Disable JavaScript
Disabling JavaScript can prevent certain attacks, such as cross-site scripting (XSS) and clickjacking. However, be aware that disabling JavaScript may affect the functionality of some websites. This again is, of course, nothing that is limited to Tails OS — Look into the uBlock Origin plugin for your everyday needs

7. Avoid Traffic Analysis
Be cautious of traffic analysis techniques that can reveal your identity even when using anonymous networks like Tor or I2P. Avoid patterns in your browsing behavior that may unveil your identity.
8. Use SSH Keys
When sending data over unsecured connections like FTP or Telnet, use SSH keys to protect your identity and encrypt the transmitted information.
Closing Remarks
Tails OS is designed to provide users with enhanced security and privacy features. It routes internet connections through the Tor network, uses encryption for data storage, and leaves no traces on the host system. However, it’s important to remember that no operating system is completely invulnerable to attacks. Practicing safe browsing habits, updating software, and being aware of potential threats is still crucial. Tails OS is a powerful tool, not a substitute for responsible online behavior.
As the makers of Tails OS say it: “Tails is safe but not magic!” — No tool, no OS, is perfect; none of the available tools or Operating systems can provide 100 percent security, privacy, or anonymity. Nation States have such vast resources at their disposal that you can assume they can find out who you are if they want to.
A few more resources
And some related topics:
