The Twitter (X) Attack - The Affiliation and Operations of the Dark Storm Team Group

The Dark Storm Team, a pro-Palestinian hacktivist group active since at least 2023, has become more busy recently, targeting Israel, Western nations, and NATO-aligned entities. However, the biggest noise they made was yesterday's DDOS attack on Twitter (X). Elon Musk was quick to blame the attack on the Ukraine, but, looking at Dark Storm Team in detail suggests that nothing could be further from the truth. What, Musk is peddling fake news and misinformation? SHOCKER (not).
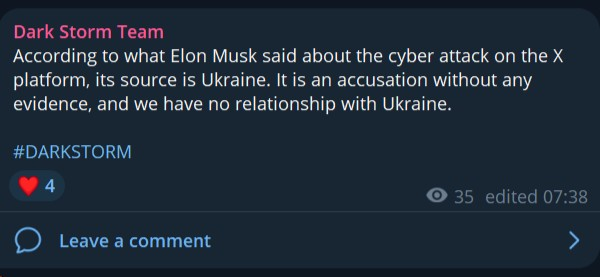
While their public rhetoric emphasizes opposition to Israeli military actions in Gaza, cybersecurity analysts have identified potential affiliations with Russian cyber units and state-aligned interests. The group’s activities—ranging from distributed denial-of-service (DDoS) attacks to data leaks and paid cybercriminal services—reflect a dual agenda combining political hacktivism and commercial motivations.
Origins and Ideological Foundations
Emergence and Pro-Palestinian Stance
The Dark Storm Team first surfaced around 2023, positioning itself as a pro-Palestinian collective opposed to Israel’s military operations in Gaza. During their early campaigns, the group targeted Israeli government infrastructure, including Haifa Port, and expanded to strike entities in Europe and the United States perceived as supporting Israel. The group’s Telegram communications (recently banned but since resurfaced) often frame their actions as retaliation for civilian casualties in Palestinian territories, leveraging emotive narratives to garner support within hacktivist circles.
A closer look however, suggests that the group’s activities extend beyond pure ideological motivations. Dark Storm Team monetizes its operations through paid cybercrime services, including ransomware deployment and data brokerage, suggesting a hybrid model blending activism and profit3. This duality complicates assessments of their true objectives, as financial incentives may drive targeting decisions as much as political allegiances.
Structural and Operational Characteristics
Dark Storm Team operates as a decentralized collective, recruiting members through different encrypted platforms like Telegram as well as the dark web. Their operational security protocols include the use of obfuscated communication channels and cryptocurrency payments to obscure financial trails. The group has developed proprietary tools, such as customized DDoS botnets, which they deploy against high-value targets. During yesterday's Twitter (X) outage, Dark Storm leveraged a globally distributed botnet to overwhelm the platform’s servers, demonstrating advanced technical capabilities. They shared the usual "Evidence" in the form of screenshots:
Affiliations and Geopolitical Alignment
Links to Pro-Russian Cyber Networks
Multiple independent analyses identify Dark Storm Team as having “highly likely” ties to Russian cyber units. Orange Cyberdefense highlights the group’s collaboration with pro-Russian hacktivist collectives, including NoName057(16)—a group known for DDoS attacks on Ukrainian and NATO infrastructure.
https://www.orangecyberdefense.com/global/insights/research-intelligence/epidemiology-labs
These partnerships enable resource-sharing, such as access to Russian-hosted botnets and exploit databases, amplifying Dark Storm’s operational reach.
The group’s alignment with Russian interests is further shown by their targeting patterns. While primary attacks focus on Israeli and Western entities, secondary campaigns have disrupted critical infrastructure in countries opposing Russia’s geopolitical agenda, such as Ukraine and Baltic states. This targeting pattern perfectly aligns with the Kremlin’s strategy of using proxy groups to destabilize adversaries without direct attribution, a fact obviously lost to Elon Musk, or, at least a fact not suitable for his own agenda, hence the quick accusation of Ukraine as being behind the attack.
Potential State Sponsorship
Elon Musk’s characterization of the March 2025 X attack as a “massive cyberattack” involving “nation-state” resources has fueled speculation about Dark Storm’s state affiliations. Musk was not wrong with that part of his statement, even though his accusing of Ukraine being behind it could not be further from the truth. The scale and sophistication of the attack—which required coordination across hundreds of thousands of IP addresses—exceed the typical hacktivist capabilities, suggesting external resourcing. Cybersecurity analysts posit that Dark Storm may function as a semi-autonomous proxy for Russian intelligence agencies, mirroring the relationship between groups like Fancy Bear (GRU Unit 26165) and the Russian government.
Having said all that, I need to add that actual evidence that can link Dark Storm to the Russian government remains elusive. Unlike groups such as Fancy Bear, which often show clear operational ties to military intelligence structures, Dark Storm’s connections appear informal, based on tactical collaboration rather than hierarchical control. This ambiguity allows the group to maintain plausible deniability while advancing Russian strategic interests. It also allows the same plausible deniability to the Russian state.
Operational Tactics and Notable Campaigns
DDoS as a Primary Weapon
Dark Storm Team’s signature tactic are large-scale DDoS attacks, which they employ to cripple target networks. Their attack on Twitter (X) flooded the platform’s servers with 1.2 terabits per second of traffic, triggering three global outages within 24 hours. The attack leveraged a combination of IoT device botnets and cloud service exploitation, bypassing conventional mitigation measures until Twitter (X) implemented Cloudflare’s advanced DDoS protection.
Data Exfiltration and Psychological Warfare
Beyond disruption, the group engages in data theft to undermine institutional trust. In a 2024 campaign, they breached the UAE Ministry of Defense, exfiltrating sensitive documents related to regional security cooperation with Israel. Leaked files were disseminated through Russian-aligned disinformation networks, amplifying their psychological impact.
Adaptive Threat Infrastructure
Dark Storm’s infrastructure exhibits notable adaptability. During the Twitter (X) attack, they dynamically shifted command-and-control servers across jurisdictions, exploiting legal asymmetries in cybercrime enforcement. The group also employs blockchain-based DNS services to maintain resilience against takedown attempts, a tactic pioneered by Russian state-sponsored actors.
Geopolitical Implications and Future Trajectory
Escalating Cyber-Physical Convergence
The group’s evolving capabilities raise concerns about cyber-physical convergence. In January 2025, Dark Storm infiltrated supervisory control and data acquisition (SCADA) systems at a European water treatment plant, briefly disrupting operations. While the attack caused no actual physical damage, it demonstrated potential to cross the digital-physical threshold—a red line in critical infrastructure protection.
Western Countermeasures and Attribution Challenges
Responses to Dark Storm’s activities have been hampered by the challenge of attributing the attacks. Despite forensic evidence linking their tools to Russian cyber arsenals, the lack of definitive state fingerprints complicates diplomatic and legal responses. The United States Cyber Command has reportedly deployed counter-botnet operations to degrade Dark Storm’s infrastructure, but these measures remain reactive rather than preventive.

Prognosis: Deepening Russia Alignment
The latest observations and developments suggest Dark Storm Team will deepen its ties with Russian cyber networks. The group’s Telegram channels have increasingly echoed Kremlin narratives, framing NATO expansion as a existential threat and endorsing Russian military actions in Ukraine.
If you like my articles. buy me a coffee to keep me going 😄


